 This blog has been receiving lots of traffic lately to a post on using AWS Route 53 DNS in a VPC. Google features the post in search results for folks interested in the topic and I am gratified that people find it and spend long periods (sometimes more than 20 minutes) reading it — and I presume — implementing the technique.
This blog has been receiving lots of traffic lately to a post on using AWS Route 53 DNS in a VPC. Google features the post in search results for folks interested in the topic and I am gratified that people find it and spend long periods (sometimes more than 20 minutes) reading it — and I presume — implementing the technique.
But with AWS, things move fast and in November 2014 AWS announced that Route 53 now supports private DNS in Route 53.
I was excited by this announcement and have spent some time working with the new capability in a test VPC. Over time, I think this new capability will make managing EC2 instances in VPCs by name much easier. But one specific need isn’t in the initial release of the product and I hope AWS adds it soon.
I manage a large Windows environment in AWS. We are beginning to implement Active Directory to provide SSO for users of the applications we are deploying.
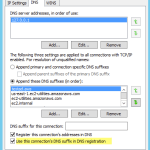
In an AWS VPC, you pretty much must use the AWS-provided DHCP server which is no problem to integrate with AD DS. And, when you use the AWS DHCP server and assign fixed private addresses to your instances, you actually need not worry about assigning static IP addresses in your Windows instances — a major plus, IMO. You can just leave the adapters set to obtain addresses automatically for both the local adapter and the DNS server. (You should, however, be sure to set “Use this connection’s DNS suffix in DNS registration” on AD DS domain controllers. It’s not the default. See image below.)
But one thing that’s beyond most Windows AD DS admins’ capabilities or desires — and is certainly something one should never try lightly — is using an external DNS server with Windows AD DS. To describe the dependencies AD DS has on DNS takes several chapters of your favorite Windows Server “in-depth” guide. Bottom line: you probably should use Windows Server DNS with AD DS and when you install AD DS, Server Manager will default to installing Windows DNS with AD DS. (AWS recommends installing DNS on each domain controller which is a wise choice for EC2 domain controllers.)
In the typical EC2 setup your Windows instances use your instance’s DNS and you set the Windows DNS to forward requests for zones to the AWS DNS (at the “plus-two” address in your VPC by default, e.g. 10.0.0.2 for a 10.0.0.0/16 VPC). (You could also check the “use root hints” in your Windows DNS without explicitly forwarding to the AWS DNS to resolve names outside the VPC, but I think that’s less performant than using the AWS DNS.)
Now that we have that straight, the question becomes: can we get the AWS private DNS to delegate incoming DNS requests to the Windows Server DNS? How cool would that be? Answer: very.
We could use this capability with Remote Desktop Gateway, for example, to allow us to specify the private name of the target RDP session by using the Windows DNS internal FQDN of the machine.
IOW, we’d only need two sets of names — names in our “real” external Route 53 zone and a “root” private Route 53 zone which could delegate requests to a Windows Server DNS. You could separate all the private addresses into the Windows Server DNS, replicate those to all your domain controllers and never need to add the internal addresses to the Route 53 private zone And, you’d only need to set up the delegation in Route 53 once. Then, you could resolve any internal name from any instance — even Linux instances — using AD integrated DNS zones.
But, alas, as you can see from this question I asked on the Route 53 forum, Route 53 doesn’t yet support this.
AWS, if you are listening, this would be a great addition to Route 53, especially for Windows AD DS users who run AD in EC2.
Leave a Reply