One of the curses of being a cloud infrastructure architect, engineer or developer is logging in and out of hosts…in and out….and in and out. This session here; that session there. A dozen RDP sessions to Windows Server EC2 instances plus many, many ssh sessions clutter your RDP manager and ~/.ssh/config. #DevOps folks are afflicted by an endless cycle of access. Compounding the problem: databases and authenticated APIs. Creds are the keys to the kingdom.
So, what to do? You probably don’t wanna admit what you are currently doing: store the creds somewhere you shouldn’t and use them however you like. C’mon…I’ve done it and so have you. It’s convenient. It’s easy. But it’s also massively insecure.
We have got to stop doing this for infrastructure management. But we also still need to do our jobs. So something’s gotta change.
Today, @HashiCorp showed off Boundary at Security Tech Field Day 9 #XFD9. Extending the company’s reputation as one of the pioneers of DevOps tooling for cloud-first dev teams, Boundary solves the infrastructure access convenience and security problems in one fell swoop.
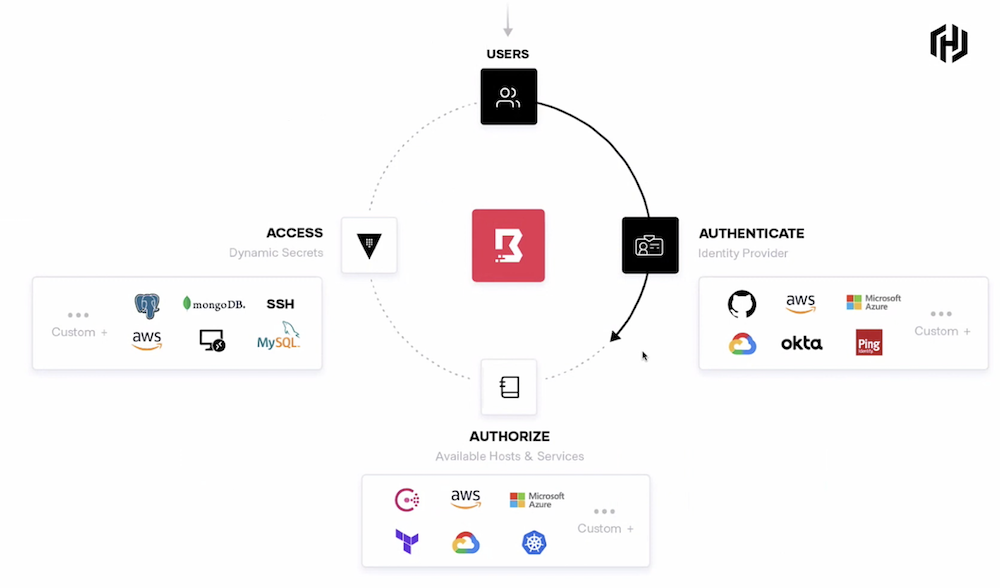
Boundary scores a double-punch against these two scourges by leveraging cloud-native network constructs in combination with scalable proxying. As shown in a live demo today (be certain to watch this on the #XFD9 website…and props to HashiCorp keepin’ the faith and showin’ live product), Boundary makes a compelling case. Consider:
- A control plane is able to sum together all the claims from a series of back-end identity providers (LDAP being newly available here) into a combined account that represents all the desired policies (represented by claims) for that user. These secrets can be time-limited.
- An elegant proxying environment for SSH and RDP sessions — which can be chained to support complex VPC topologies — runs under the organization’s control, ensuring integrity of the sessions that have been authenticated and authorized.
- A still-evolving session recording feature helps with audit — and can show you exactly when you deleted
/etc/passwd. 🙂
There’s too much functionality to get into a blog post, of course. And I want to make sure to mention that, as is typical for HashiCorp, the product is open source and has both a self-hosted and managed-service offering.
I’m excited about Boundary. It does that thing that’s so hard to do and is the mark of usefulness: it solves a problem that you and I live with every day in a verifiably secure manner. That it’s also open source means that its internals are auditable, an important consideration for enterprise users before trusting a product in this category.
You get the feeling listening to the Boundary product engineers and product managers that they have a much more expansive set of functionality on their roadmap beyond simple infrastructure access management.
Until then, I’m changing “login shampoos”…from the rinse, repeat…rinse, repeat category to the all-in-one category, called Boundary.
Leave a Reply